Network segmentation is hard.
It shouldn't be.
Experience a Segmentation Solution That Actually Lives Up to Its Promises
When 9 out of 10 segmentation projects struggle to meet expectations, Elisity redefines what’s possible. Our identity-based approach shatters the complexity barrier, delivering unrivaled visibility, control, and compliance across your entire network.
Message from the CEO: Elisity Secures $37M to Pioneer Identity-Centric Security Solutions Learn More -->
"Elisity's deployment at GSK is nothing short of revolutionary making every other solution pale in comparison."
Overcome the Challenges of Securing Modern Networks
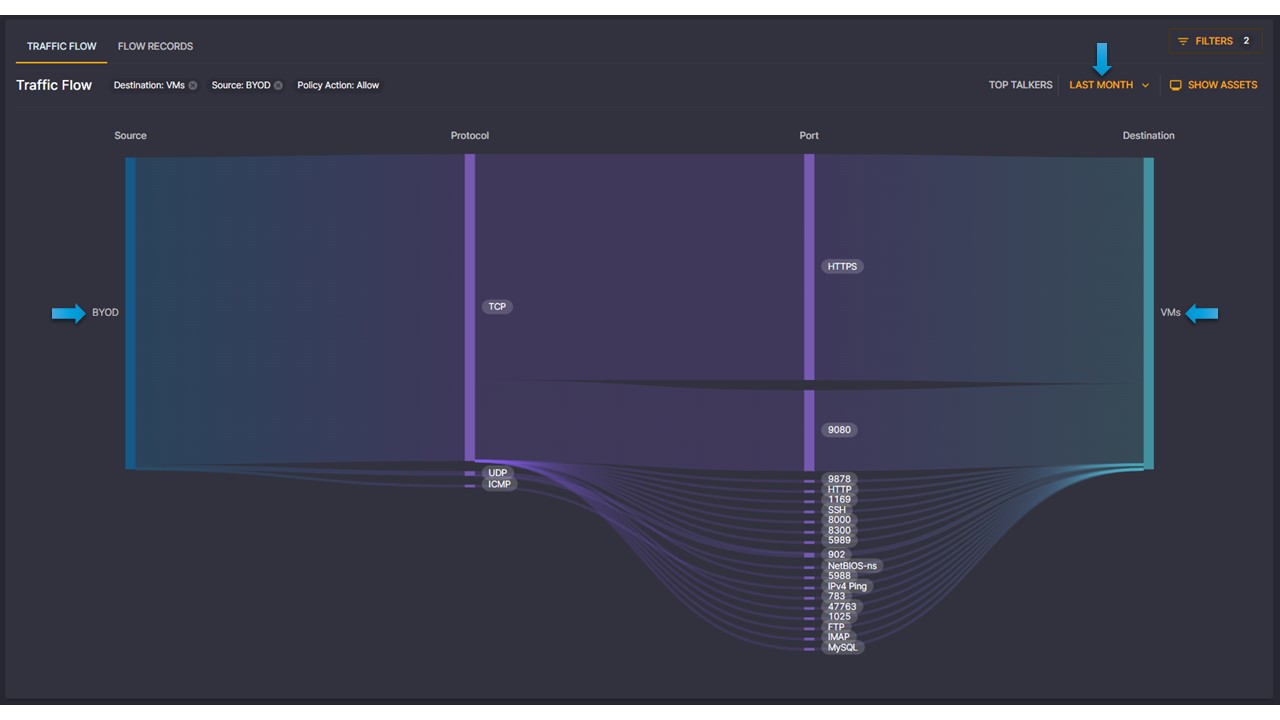
Gain unparalleled visibility into your network with Elisity’s IdentityGraph technology, and leverage identity-based microsegmentation to enforce granular control over every user and device. By utilizing identity attributes and dynamic contextual policies, you can implement robust network segmentation, a crucial defense strategy against modern threats and ransomware, effectively limiting the blast radius of potential attacks.
Core Benefits
Comprehensive Visibility
Granular Control
Lateral Movement Defense
Simplified Management
Continuous Compliance
Zero Trust Enablement

GSK is Deploying Elisity with Unprecedented Speed
“Elisity’s deployment at GSK is nothing short of revolutionary, making every other solution pale in comparison.”

Michael Elmore
CISO at GSK
Minutes
With a striking speed of less than 30 minutes per location, Elisity's integration is bolstering GSK's operations like never before.
Sites Per Week
As GSK rides the wave of global expansion, it successfully initiates three new Elisity-powered sites every week.
Integrations
Our engine powered by AI is capable of discovering, classifying, and monitoring devices and users. It collects device identity data from various sources such as Active Directory, Crowdstrike, Claroty, Armis, and more, which helps to create a context for enforcing identity-based policies. Additionally, our platform integrates with popular access switches from Cisco, Arista, and Juniper.











“Elisity’s identity-based microsegmentation brings tremendous capabilities to our security stack as a critical control point for containing ransomware, blocking malicious lateral network traffic and minimizing incident blast radius, and Elisity features prominently for our present and forward-looking security posture, allowing us to easily adjust to new regulatory as well as threat landscape developments.”

Aaron Weismann
CISO at Main Line Health
“We deployed it at two of our sites in less than an hour, and by the next day, we were confidently implementing policies. This unprecedented speed and effectiveness soon made Elisity an indispensable part of our network security strategy across our manufacturing sites, protecting thousands of managed IT assets as well as our growing number of unmanaged IoT and OT assets.”

Max Everett
CISO at Shaw Industries
“In my 30 years of working in technology and security, I’ve never delivered a product into an environment and got instant benefit like we did with Elisity.”

Paul Haywood
CISO at Bupa Health
“Elisity’s solution is a game-changer. Its intelligent asset classification, visibility and rapid policy enforcement have allowed us to monitor and secure our network in ways we couldn’t have imagined.”

Steve Garske, PhD, MSc, MBA
CIO & CISO at Logan Health
Customers who Trust Elisity



Industries
Scalable Industrial Defense
Flexible security for large-scale industrial operations.
Secure Patient Care
Protect against lateral movements, safeguard patient care.
Reliable Business Continuity
Safeguard all IT and IoT assets with comprehensive solutions.
Stay up to date with the latest news

Elisity Raises $37M Series B to Fuel AI Innovation in Identity-Based Microsegmentation
Identity-based approach to microsegmentation speeds adoption in OT, IoT and hybrid…
Elisity Named Among Notable Vendors in the Forrester Microsegmentation Landscape, Q2 2024
We are thrilled to announce that Elisity has been named a notable vendor in Forres…

Elisity Secures $37M to Pioneer Identity-centric Security Solutions
Today marks a significant milestone for Elisity, as we proudly announce $37 millio…