IEC 62443 Segmentation with Elisity: Enhancing Industrial Control Systems Security
- Introduction
- Background: IEC 62443, Purdue Model, and Segmentation
- Elisity: A Modern Solution for IEC 62443 Segmentation
- Use Case: Implementing IEC 62443 Segmentation with Elisity
- Defining Zones and Subzones with Policy Groups
- Building Conduits with the Elisity Policy Matrix
- Key Benefits of Elisity’s Solution
- Conclusion
Introduction
Key Findings
Industrial control systems (ICS) are not exempt from known and unknown vulnerabilities, targeted attacks, phishing attempts, malware, and ransomware. The IEC 62443 standard places great emphasis on the importance of effective segmentation within IT and OT environments. In this solution brief, we’ll explore how Elisity can help organizations meet the segmentation requirements of the IEC 62443 standard and secure their industrial control systems.Download this White Paper
Background: IEC 62443, Purdue Model, and Segmentation
The IEC 62443 standard and the Purdue model focus on the importance of segmentation in securing industrial control systems. Segmentation involves breaking down a process control network (PCN) into smaller, more secure segments. Microsegmentation allows for a more granular level of security by creating separate access policies for different industrial devices and systems within a production environment.
Traditional segmentation methods like firewalls and data diodes struggle to scale with the increasing complexity of modern networks. The IEC 62443 standard recommends implementing Zones, Subzones, and Conduits for effective segmentation.
Download this Solution Brief
Elisity: A Modern Solution for IEC 62443 Segmentation
Elisity enables organizations to confidently and automatically identify and group their critical assets, define zones or sub-zones, and build conduits to meet the IEC 62443 standard requirements without causing any loss of service.
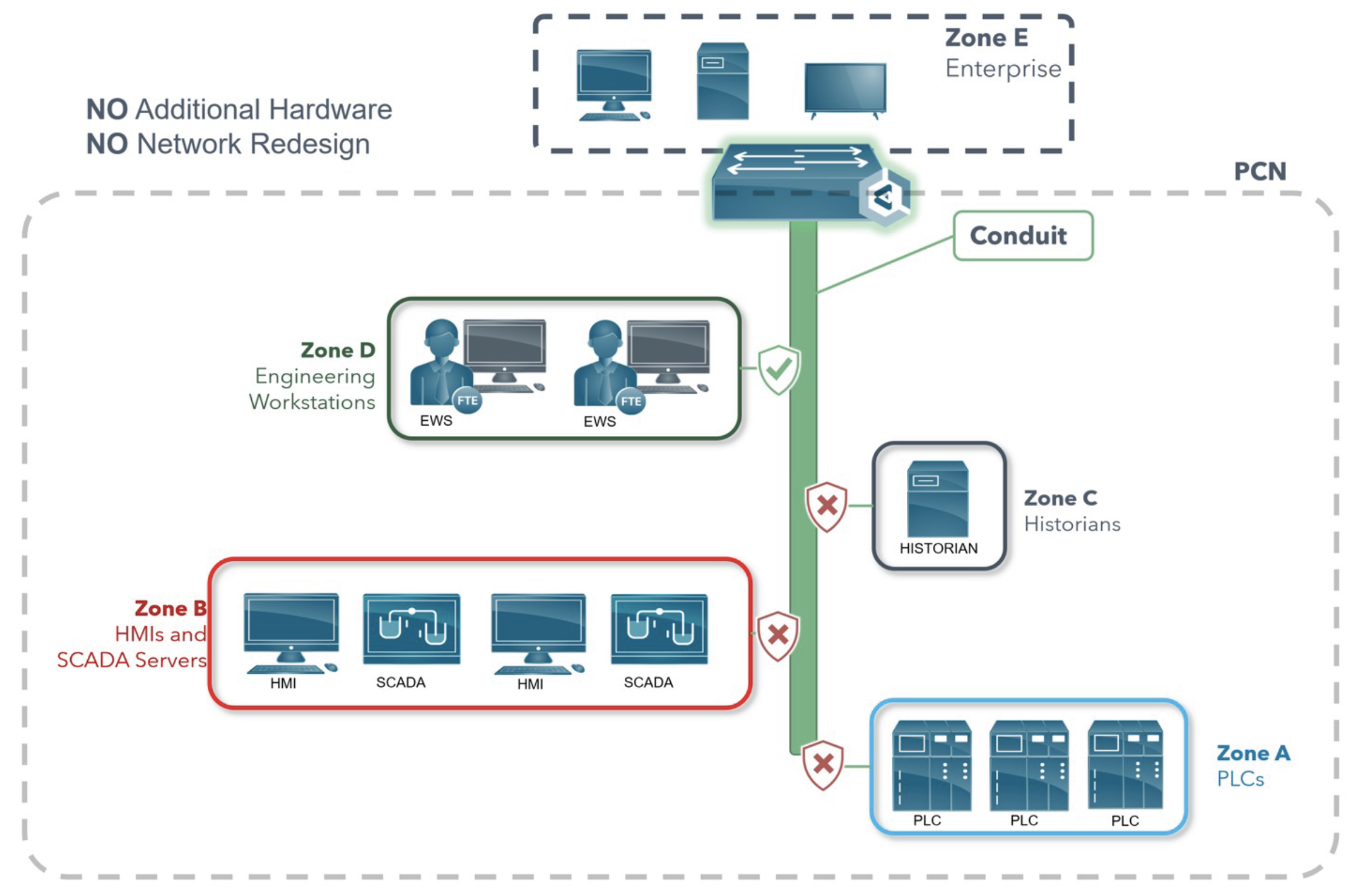
Use Case: Implementing IEC 62443 Segmentation with Elisity
In this example, an OT security engineer is tasked with implementing a segmentation strategy that complies with IEC 62443. The goals are to:
- Identify and group network-connected assets and their attributes.
- Create Zones and Sub-zones based on shared security requirements or business needs.
- Define security policies within and between Zones and Sub-zones to control access and communication channels.
Elisity achieves these goals by leveraging existing access infrastructure to overlay virtual zones and conduits without requiring additional hardware or disrupting the production network.
Defining Zones and Subzones with Policy Groups
Elisity uses Policy Groups to define Zones and Subzones by grouping assets based on a set of match criteria specified by the operator. These criteria leverage the asset attributes collected by Elisity, which can be enriched through integration with third-party asset identification engines such as Claroty and CMDBs like ServiceNow.
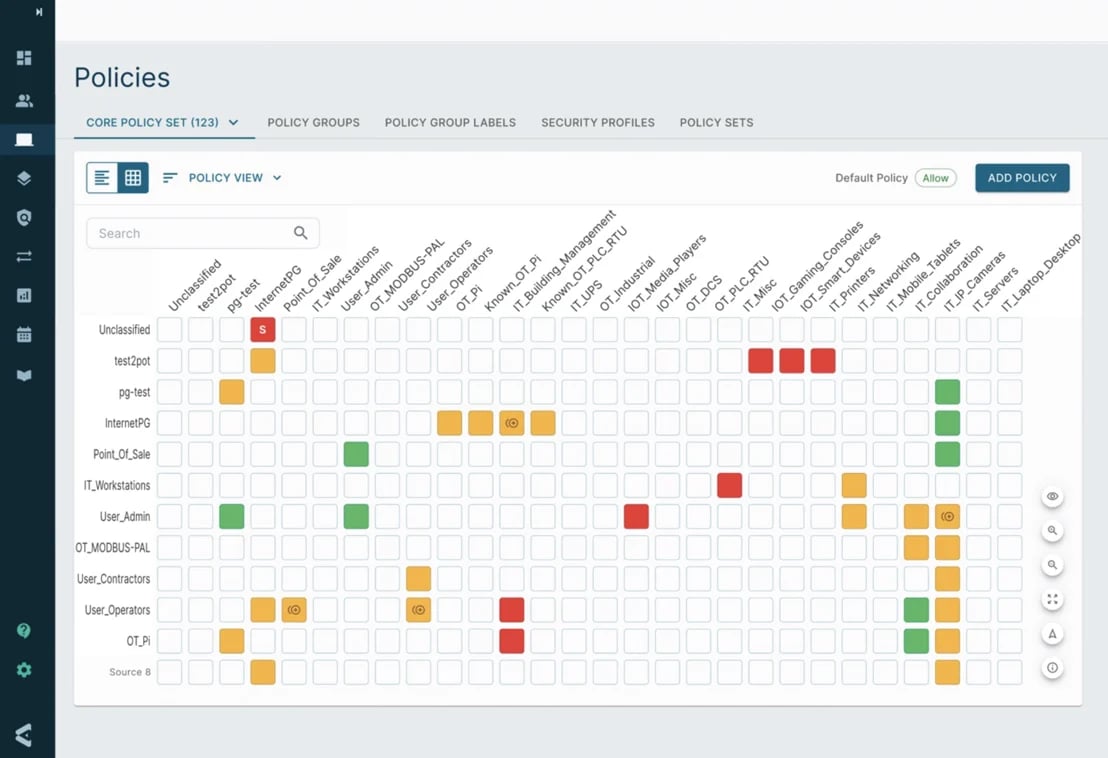
Building Conduits with the Elisity Policy Matrix
The Elisity Policy Matrix allows the OT security engineer to define the trusted and untrusted conduits within and between Zones and Subzones based on their mapped communication needs.
Key Benefits of Elisity’s Solution
Elisity's solution offers a powerful and flexible approach to implementing IEC 62443 compliant segmentation in OT environments. Its innovative use of virtual zones, conduits, and integration with third-party systems provides numerous benefits for organizations seeking to enhance their ICS security. Here are the key benefits of using Elisity's solution:
- Simplified and Granular Segmentation: Elisity's solution enables organizations to implement granular segmentation without the need for complex hardware configurations or manual intervention. By leveraging asset attributes, users can create policy groups to define zones and subzones with unparalleled precision. This makes it easier to achieve a least privilege access architecture and maintain compliance with IEC 62443.
- Scalability and Flexibility: Elisity's approach to segmentation is highly scalable and adaptable to changing business and technical requirements. The virtual nature of zones and conduits allows for rapid adjustments without disruption to the production network. This means organizations can easily add, remove, or modify zones and conduits as needed.
- Enhanced Visibility and Control: By integrating with third-party asset identification engines, such as Claroty, and CMDBs like ServiceNow, Elisity offers enhanced visibility into network assets and their attributes. This enables security engineers to gain a comprehensive understanding of the OT environment and maintain up-to-date security policies.
- Improved Security for Users: Through integration with Active Directory and other user management systems, Elisity provides selective access to network resources based on user attributes. This ensures that only authorized personnel can access critical assets, reducing the risk of unauthorized access or insider threats.
- Reduced Complexity and Cost: Elisity's solution eliminates the need for additional hardware, such as firewalls or data diodes, and reduces the reliance on traditional network constructs like VLANs and VRFs. This results in lower costs and reduced complexity for organizations, allowing them to focus on maintaining a secure OT environment.
In summary, Elisity's solution offers a modern approach to IEC 62443 compliant segmentation that simplifies the process, increases security, and reduces the costs and complexity typically associated with traditional segmentation methods. By leveraging virtual zones, conduits, and integration with third-party systems, organizations can confidently implement a robust ICS security strategy.
Conclusion
With Elisity, organizations can meet the IEC 62443 standard requirements for segmentation while gaining visibility into their PCN, refining security zones without heavy lifting, and controlling traffic between physical zones. By leveraging existing access infrastructure, Elisity provides a scalable and modern solution for ICS security.
Download this Solution Brief
From Our Blog
Stay up to date with what is new in our industry, learn more about the upcoming products and events.

Leveling Up: Women Redefining Success in Cybersecurity

Microsegmentation Case Study: How Andelyn Biosciences Accelerated Zero Trust in Weeks, Not Years
