Share this
Maximizing Security with Elisity Cloud Control Center 15.7: Key Features and Real-World Use Cases
by Taylor Colwell on Jul 2, 2024 3:14:19 PM
Introduction
The latest 15.7 release of Elisity Cloud Control Center introduces powerful enhancements that significantly boost security and simplify management. This release brings advanced features such as Asset Locking in Policy Groups, Local Policy Groups, and enhanced Role-Based Access Control (RBAC), offering innovative solutions to some of the most pressing challenges in network security and management.
Elisity stands out because of the unparalleled granular control these new enhancements provide. With Asset Locking in Policy Groups, you can ensure that critical assets remain securely bound to their designated policy groups, no matter how network identities change. Local Policy Groups enable you to implement and manage security policies tailored to specific network segments with remarkable ease, ensuring precise protection where it's needed most. The enhancements to RBAC allow you to finely control user access to sites, settings, assets, and APIs, minimizing the risk of unauthorized changes and significantly strengthening overall security.
In this post, we'll explore these groundbreaking features, diving into real-world use cases that demonstrate their practical benefits. Whether you're looking to protect vital infrastructure, manage security policies for different locations, or streamline access control, the 15.7 release offers the tools you need to elevate your security strategy.
Join us as we uncover how these new features can transform your approach to network security and management, providing you with the confidence and control to protect your organization effectively.
1. Asset Locking in Policy Groups
Feature Description
Asset Locking in Policy Groups is a pivotal feature in the 15.7 release of Elisity Cloud Control Center. This feature ensures that once an asset is assigned to a specific Policy Group, it remains securely bound to that group, regardless of changes in network identity or policy attributes. This capability is crucial for maintaining consistent security policies for assets where reclassification could lead to severe security breaches or compliance issues. While it requires manual configuration, the benefits of asset locking are indispensable for securing critical assets in dynamic network environments.
By locking an asset to a Policy Group, administrators can confidently use dynamic match criteria without worrying that essential assets will be reclassified based on network changes or identity updates. This ensures that the security posture of these assets remains intact, providing an added layer of protection.
There are three specific scenarios where this is applicable:
- Changes to match criteria in Policy Groups
- Changes to device attributes
- Changes to Policy Group priority
Any of these changes can result in a device being reclassified using dynamic Policy Groups. In many cases, this behavior is advantageous as it introduces a level of automation, ensuring that changes in Identity result in changes in network privileges. However, for specific assets which perform critical functions, a change in Policy Group association can have unintended consequences that could potentially cause disruptions in critical processes and business operations. Asset Locking alleviates these concerns for those critical assets that must maintain consistent classification and policy enforcement.
Technical Details
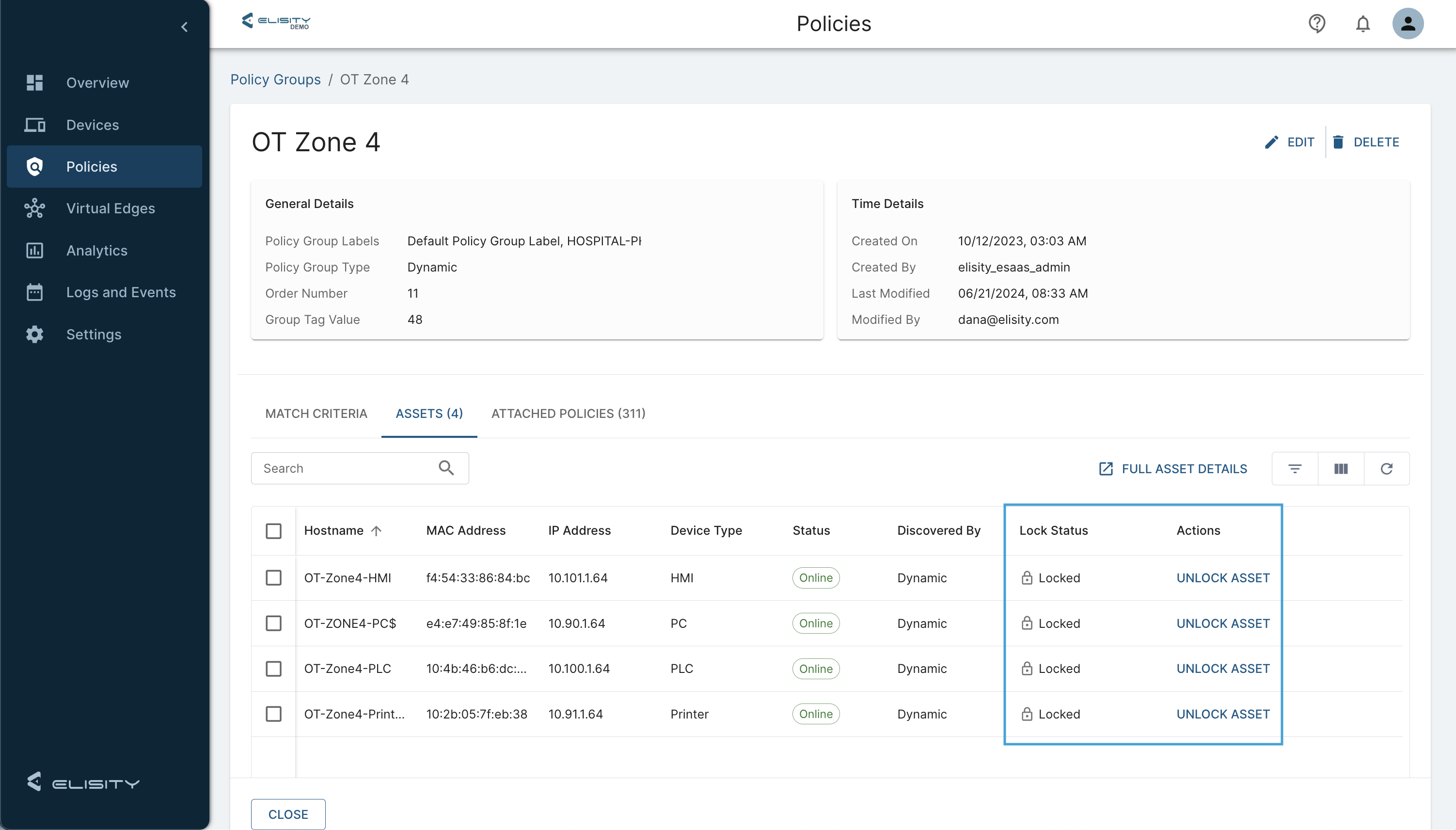
Implementing asset locking in Policy Groups within the Cloud Control Center involves the following steps:
- Navigate to the Policy Groups Section: In the Cloud Control Center, go to the Policy Groups section where you manage your security policies.
- Select the Asset: Identify and select the asset you want to lock within its current Policy Group.
- Enable Asset Locking: Utilize the asset locking option to bind the asset to its current Policy Group.
- Confirm the Configuration: Ensure that the asset is now marked as locked, preventing it from being reclassified into other Policy Groups.
Use Case: Protecting Industrial Control Systems (ICS) in Manufacturing
Scenario: A manufacturing company relies on Industrial Control Systems (ICS) to manage and monitor its production lines. These systems are integral to the operation of critical processes and the overall productivity of the facility.
Challenge: Changes in the network environment, such as updates to device attributes or modifications to Policy Group criteria, could inadvertently reclassify these critical ICS devices into different Policy Groups. Such reclassification can lead to unintended consequences, disrupting manufacturing operations and potentially causing significant downtime.
Implementation: The IT security team locks these ICS devices into specific Policy Groups that are tailored to their critical roles within the production environment. This includes stringent access controls, continuous monitoring, and robust threat detection measures to ensure the highest level of security.
Benefits: By using asset locking, the manufacturing company ensures that its ICS devices remain in their designated Policy Groups, maintaining consistent and reliable security measures. This approach minimizes the risk of operational disruptions due to unintended reclassification, ensuring that critical processes continue without interruption. The ability to confidently use dynamic match criteria for other assets without affecting these locked devices provides a balanced approach to both flexibility and security.
By leveraging Asset Locking in Policy Groups, organizations can protect their most critical assets from unintended reclassification, ensuring consistent and robust security policies. This feature is essential for environments where reclassification events could have dire consequences, allowing dynamic policy management without compromising the security of key assets.
Local Policy Groups
Feature Description
Local Policy Groups in the 15.7 release of Elisity Cloud Control Center provide a powerful tool for managing network security at a granular level. Unlike global Policy Groups, which apply universally across the entire network, Local Policy Groups allow administrators to define asset groupings specific to individual sites. This feature is crucial for environments where certain sites have unique or varying assets that require specialized security policies.
With Local Policy Groups, administrators can create distinct asset groupings for each site that take precedence over Global Policy Groups. This capability ensures that sites with unique security requirements are adequately protected without impacting the broader network policy. It offers the flexibility to tailor security measures to the specific needs of each location, enhancing overall network protection and operational efficiency.
Technical Details
Implementing Local Policy Groups within the Cloud Control Center involves the following steps:
- Enable Local Policy Groups: Enable Local Policy Groups by navigating to the Settings > Advanced page in Cloud Control Center.
- Access the Policy Groups Section: Navigate to the Policy Groups section in the Cloud Control Center.
- Create a New Local Policy Group: Select the option to create a new Local Policy Group.
- Assign Site-Specific Labels: Specify the site label for the Local Policy Group to ensure it applies only to the designated site.
- Define Asset Groupings: Group assets specific to the site within the Local Policy Group.
- Configure Policies: Set up the security policies for the Local Policy Group, ensuring they meet the unique requirements of the site.
- Deploy the Local Policy Group: Save and deploy the Local Policy Group to enforce the policies on the specified site.
Real-World Use Cases
Use Case 1: Branch Office Security for a Retail Chain
Scenario: A large retail chain operates multiple branch offices across different regions, each with its own network infrastructure and unique assets.
Challenge: Applying the same Policy Groups across all branches may not adequately protect assets specific to certain locations, leading to potential security vulnerabilities.
Implementation: The IT security team uses Local Policy Groups to create asset groupings tailored to each branch office. For example, a branch office in a high-traffic area might have a Local Policy Group that includes additional security cameras, point-of-sale systems, and inventory management systems, all protected under a customized security policy.
Benefits: By using Local Policy Groups, the retail chain ensures that each branch office's unique assets are adequately protected. This targeted approach enhances security for location-specific assets, reduces the risk of security breaches, and optimizes resource use. The flexibility to adjust policies based on local needs ensures comprehensive protection without impacting the broader network security posture.
Use Case 2: ICS and Manufacturing
Scenario: A manufacturing company operates several facilities, each with distinct operational requirements and critical assets, such as specialized machinery, control systems, and sensors.
Challenge: Uniform Policy Groups may not provide the necessary level of security for unique assets in different facilities, leading to potential vulnerabilities in critical zones.
Implementation: The IT security team leverages Local Policy Groups to create asset groupings specific to each manufacturing facility. For example, a facility that produces high-value products might have a Local Policy Group for its specialized machinery and control systems, with stringent security policies that include restricted access, continuous monitoring, and enhanced threat detection.
Benefits: Local Policy Groups enable the manufacturing company to implement precise security measures for each facility's unique assets. This granular control helps protect critical processes from potential threats, ensures compliance with industry regulations, and optimizes the overall security posture. The ability to easily adjust policies as operations evolve ensures that security measures remain effective in a dynamic environment.
By utilizing Local Policy Groups, organizations can achieve a higher level of security customization and flexibility. This feature allows for the precise application of security policies tailored to the unique needs of different sites, enhancing overall protection and operational efficiency. The ease of managing Local Policy Groups through Elisity Cloud Control Center further highlights its value, making advanced network segmentation accessible and practical for a wide range of organizations.
3. Role-Based Access Control (RBAC)
Feature Description
Role-Based Access Control (RBAC) in the Elisity Cloud Control Center 15.7 release brings enhanced capabilities for controlling user access to network resources. RBAC allows administrators to assign specific permissions to users based on their roles within the organization, providing a fine-grained approach to access management. This feature is essential for maintaining security, ensuring compliance, and reducing the risk of unauthorized changes within the Cloud Control Center.
The enhancements to RBAC in this release extend beyond basic user access control, encompassing sites, settings, assets, Policy Groups (PGs), and APIs. Each endpoint in the Cloud Control Center can be secured based on the RBAC role assigned to the user or API client, ensuring that access is granted only where necessary and appropriate. These roles can be mapped to user groups in your SSO provider, enabling RBAC for SSO login access to Cloud Control Center.
Technical Details
Setting up and configuring RBAC in the Cloud Control Center involves the following steps:
- Access the Admin Settings: Navigate to the Admin settings section in the Cloud Control Center.
- Define Roles: Create roles that correspond to different levels of access and responsibilities within the organization. For example, roles can be defined for site admins, network engineers, security analysts, and more.
- Assign Permissions: Specify the permissions associated with each role. This includes access to specific sites, settings, assets, Policy Groups, and APIs.
- Assign Roles to Users and API Clients: Assign the defined roles to individual users and API clients, ensuring they have access only to the resources they need.
- Review and Adjust: Regularly review and adjust the roles and permissions to accommodate changes in the organization and ensure continued security and compliance.
Real-World Use Cases
Use Case 1: Managing Access in a Large Enterprise
Scenario: A large enterprise with multiple departments and varying access needs. The organization has network engineers, security analysts, and site admins, each requiring different levels of access to the Cloud Control Center.
Challenge: Ensuring that each user has access only to the resources necessary for their role, minimizing the risk of unauthorized changes and enhancing overall security.
Implementation: The IT security team defines specific roles for each type of user. Network engineers are given access to network configuration settings and devices, security analysts have access to security logs and incident reports, and site admins have access to manage their respective sites.
Benefits: By using RBAC, the enterprise ensures that each user has the appropriate level of access, reducing the risk of accidental or malicious changes. This targeted access control streamlines operations, enhances security, and ensures compliance with internal policies and regulations. The ability to assign and manage roles through the Cloud Control Center simplifies the process, making it efficient and effective.
Use Case 2: Local Site Administration
- Scenario: A large organization with multiple sites, each managed by a local site admin. The local admins need access to manage their sites but should not have access to other sites or global settings.
- Challenge: Limiting the scope of access for local site admins to prevent unauthorized changes to other sites and global configurations.
- Implementation: The IT security team creates a role specifically for local site admins, granting them access only to the sites they manage. This role includes permissions to configure local settings, manage local assets, and view local logs, but restricts access to other sites and global configurations.
- Benefits: RBAC ensures that local site admins can efficiently manage their sites without risking unauthorized changes to other parts of the network. This reduces the potential for security breaches and configuration errors, while empowering local admins to perform their duties effectively. The clear delineation of responsibilities enhances operational efficiency and security.
By leveraging the enhanced RBAC features in the Elisity Cloud Control Center, organizations can achieve precise and secure access control across their network resources. This ensures that users and API clients have access only to what they need, minimizing the risk of unauthorized changes and enhancing overall security. The ease of managing roles and permissions through the Cloud Control Center makes RBAC an indispensable tool for modern network security management.
Conclusion
The 15.7 release of Elisity Cloud Control Center introduces powerful enhancements that provide organizations with unmatched control and security over their network environments. By leveraging features like Asset Locking in Policy Groups, Local Policy Groups, and enhanced Role-Based Access Control (RBAC), administrators can address the unique security needs of their organizations with precision and confidence.
Asset Locking in Policy Groups ensures that critical assets remain securely bound to their designated groups, maintaining consistent security policies even as network identities change. This is essential for protecting vital infrastructure and complying with stringent regulations, particularly in industries where reclassification events could lead to significant vulnerabilities.
Local Policy Groups offer granular control over network security by allowing tailored asset groupings specific to individual sites. This flexibility enables organizations to address unique security requirements for different locations, ensuring that all assets are protected according to their specific risk profiles. Whether managing a retail chain with varying security needs across branches or safeguarding critical zones in a manufacturing facility, Local Policy Groups provide the customization necessary for optimal security.
Enhanced Role-Based Access Control (RBAC) empowers organizations to finely manage user access to network resources, including sites, settings, assets, Policy Groups, and APIs. By assigning roles with specific permissions, organizations can minimize the risk of unauthorized changes and ensure that users have access only to what they need. This not only strengthens security but also streamlines operations and enhances compliance.
The 15.7 release represents a significant step forward in network security and management, offering tools that are both powerful and user-friendly. By adopting these new features, organizations can achieve a higher level of security, efficiency, and control, ensuring that their network environments are robustly protected against emerging threats.
We encourage you to explore the new features and upgrade to Elisity Cloud Control Center 15.7. Experience firsthand how these enhancements can transform your approach to network security and provide the confidence and control you need to protect your organization effectively.
For more detailed guides on each feature, visit the Elisity documentation or contact our support team for further assistance. Stay ahead of the curve with Elisity's innovative solutions and secure your network with unparalleled precision.
Share this
- Enterprise Cybersecurity (52)
- Zero Trust (21)
- Microsegmentation (16)
- Elisity (8)
- Enterprise Architecture Security (8)
- Lateral Movement (8)
- Identity (5)
- Network Security (5)
- Ransomware (5)
- Cyber Resilience (4)
- Elisity Release (4)
- Remote Access (4)
- Cybersecurity Healthcare (2)
- Identity and Access Management (2)
- Forrester (1)
- Information Security (1)
- MITRE (1)
- December 2025 (4)
- November 2025 (3)
- October 2025 (5)
- September 2025 (4)
- August 2025 (5)
- July 2025 (5)
- June 2025 (5)
- May 2025 (4)
- April 2025 (5)
- March 2025 (6)
- February 2025 (3)
- January 2025 (5)
- December 2024 (4)
- November 2024 (5)
- October 2024 (7)
- September 2024 (5)
- August 2024 (3)
- July 2024 (4)
- June 2024 (2)
- April 2024 (3)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)






No Comments Yet
Let us know what you think