Share this
Identity-Based Microsegmentation: Technical Insights from Network Field Day 36 #NFD36
by Dana Yanch on Nov 18, 2024 3:18:40 PM
At Network Field Day 36 we recently showcased a deep technical dive into the evolution of microsegmentation, featuring presentations from Elisity's leadership team. What stood out wasn't just the technical architecture but the practical approach to solving a persistent challenge: only 30% of enterprises have successfully implemented microsegmentation, despite its critical role in zero trust security.
Elisity Introduction: https://youtu.be/pJDgxx2xzeE?si=mzJgx6pabSu4BXG4
The evolution of network security and its traditional network segmentation approaches that relied on VLANs, ACLs, and firewalls has served us well for decades. However, as Piotr Kupisiewicz, Elisity's CTO, pointed out during his presentation, these tools weren't designed for today's dynamic environments where lateral movement is a technique used in 70% of ransomware attacks. The real challenge isn't just technical - it's operational. When microsegmentation projects take 1-3 years to implement, security teams face an impossible choice between protection and practicality.
Elisity Origin Story: https://youtu.be/CeH7eIzmCZg?si=ju-hkkCdNcmBK6tV
The technical sessions revealed a cloud-native approach that caught the attention of network architects. The Elisity IdentityGraph™ technology demonstrates how identity and context can be leveraged at scale, automatically discovering and correlating network assets across IT and OT environments. What makes this particularly interesting for enterprise architects is the ability to integrate with existing infrastructure - from Cisco switches to Juniper and Arista network infrastructure - without requiring forklift upgrades.
A key technical innovation highlighted during the presentations was the separation of policy management from enforcement through the Elisity Cloud Control Center and Elisity Virtual Edge architecture. This approach allows enterprises to maintain existing network topologies while adding identity-based enforcement capabilities. The Elisity Virtual Edge component can be deployed as a VM or directly on supported switches like Cisco Catalyst 9000 series, providing flexibility for diverse network environments.
Real-world implementations are perhaps the most compelling technical evidence of Elisity’s promise of Microsegmentation in Weeks, Not Years, which came from details they shared on GSK's implementation. Their journey from a traditional approach, taking 2.5 years for 1.5 sites, to achieving rapid deployments across multiple sites monthly, demonstrates the practical impact of modern microsegmentation architecture. We showed how this was achieved through automated discovery, policy simulation, and granular enforcement capabilities.
Microsegmentation Challenges and Goals Across Pharmaceutical and Healthcare Industries
https://youtu.be/MuAJxvxaM8o?si=feiI1fSk531snIcC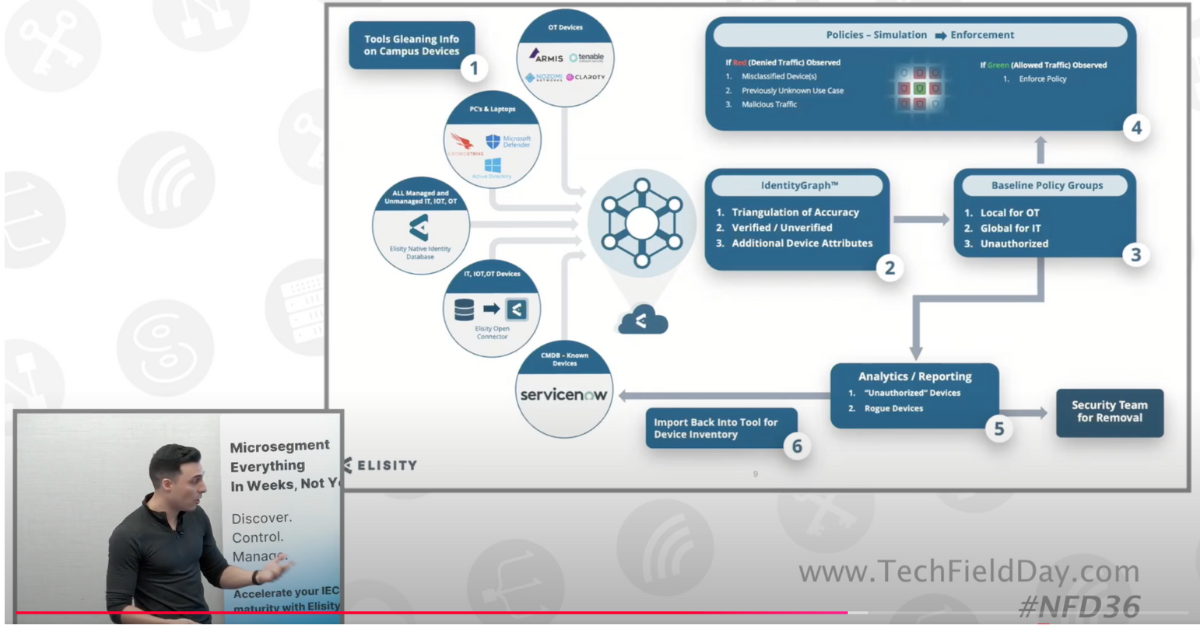
We also shared industry-specific applications for healthcare organizations. This presentation detailed how microsegmentation addresses HIPAA and 405(d) HICP compliance while protecting critical medical devices. Manufacturing environments were shown to achieve IEC 62443 compliance without disrupting production systems. The technical sessions demonstrated policy simulation capabilities that allow teams to validate segmentation rules before enforcement - a critical feature for environments where downtime isn't an option.
How to Optimize a Microsegmentation Architecture with Elisity https://youtu.be/IMlfd1J4B4U?si=sRBtBkMdp5N4GZHu 
The Elisity Dynamic Policy Engine automatically classifies and secures IoMT devices without requiring agent installations. This addresses a significant challenge in healthcare security: protecting legacy medical devices that can't support traditional security agents.
Elisity Microsegmentation Platform Demo – Clinical Healthcare Use Cases
Technical Considerations The presentations dove deep into several key technical components:
- Identity-based policy enforcement at the network edge
- Integration with existing security tools (EDR, CMDB, IoT security platforms)
- Automated asset discovery and classification
- Policy simulation and graduated enforcement
- Traffic flow visualization for policy validation
The full Network Field Day 36 videos provide detailed technical demonstrations of these capabilities, including live policy creation and enforcement examples that security architects will find particularly valuable.
As organizations progress toward zero trust architectures, microsegmentation remains a critical but challenging component. The Network Field Day 36 presentations demonstrate how modern approaches can overcome traditional implementation barriers while maintaining enterprise-grade security controls.
For security architects and technical leaders looking to accelerate their microsegmentation initiatives, the complete Network Field Day 36 session recordings provide invaluable technical insights and implementation guidance. They're particularly relevant for healthcare and manufacturing organizations dealing with complex device ecosystems and strict compliance requirements.
Watch the full Network Field Day 36 technical sessions to dive deeper into identity-based microsegmentation architecture and implementation strategies.
Next Steps On Your Microsegmentation Journey
If you want your own demo of Elisity or just want to chat about your challenges and goals with microsegmentation, schedule a call with our team here.
Share this
- Blog (30)
- Cybersecurity (13)
- Zero Trust (12)
- Enterprise Security (10)
- Identity (5)
- Elisity (4)
- Enterprise Architecture Security (4)
- Network Security (4)
- Remote Access (4)
- microsegmentation (3)
- Black Hat (2)
- Identity and Access Management (2)
- blogs (2)
- Adaptive Trust (1)
- MITRE (1)
- News (1)
- Software Supply Chain Security (1)
- case study (1)
- cyber resilience (1)
- November 2024 (4)
- October 2024 (7)
- September 2024 (5)
- August 2024 (3)
- July 2024 (4)
- June 2024 (2)
- April 2024 (3)
- March 2024 (2)
- February 2024 (1)
- January 2024 (3)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (3)
- June 2023 (1)
- May 2023 (3)
- April 2023 (1)
- March 2023 (6)
- February 2023 (4)
- January 2023 (3)
- December 2022 (8)
- November 2022 (3)
- October 2022 (1)
- July 2022 (1)
- May 2022 (1)
- February 2022 (1)
- November 2021 (1)
- August 2021 (1)
- May 2021 (2)
- April 2021 (2)
- March 2021 (3)
- February 2021 (1)
- November 2020 (2)
- October 2020 (1)
- September 2020 (1)
- August 2020 (3)

No Comments Yet
Let us know what you think