Develop a level-headed strategy
Are you a cybersecurity professional interested in Zero Trust, but don’t know where to begin? Perhaps you embarked on a Zero Trust journey with multi-factor authentication (MFA) but got stuck while test driving it in other areas, like the cloud or for remote access. The truth is that Zero Trust is a journey, and it will take time for enterprises to transition from the status quo. After all, Rome wasn’t built in one day — and you can’t undo 30 years of access strategies overnight. But the reality is that enterprises need change, and they need a place to start. Current trends in mobility, remote access, cloud, and IoT have created significant security and access problems: users need secure ways to access internal and cloud-based or SaaS apps, and devices need secure ways to talk to other devices and external applications. These problems need solving. Before you look at solutions, you need to first develop a level-headed strategy to help your organization transition smoothly to a true Zero Trust environment. We have outlined five steps that your organization can take to enable Zero Trust security across your entire digital footprint.
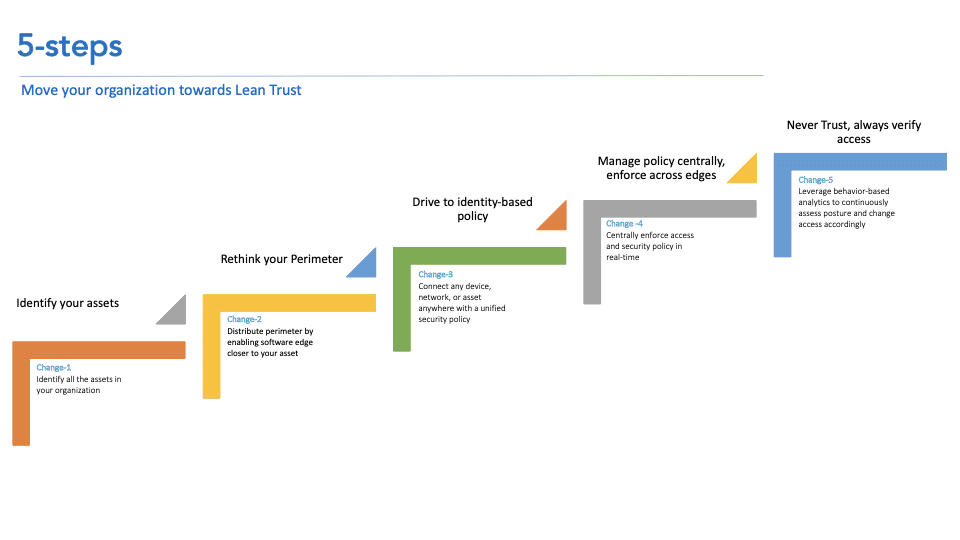
The five steps are:
- Identify your assets — the key to Zero-Trust
- Rethink your perimeter
- Transition to identity-based policy
- Manage identity-based policy centrally, enforce across edges
- Never trust, always verify access
 1. Identify all of your assets
1. Identify all of your assets
Some organizations approach Zero Trust without first gaining visibility into all of their assets. This is a mistake — and invariably these projects fail — because you can’t protect what you can’t see. To succeed with Zero Trust, enterprises need full visibility into their assets, which includes users, devices, apps, and data.
2. Rethink your perimeter
The traditional data center-as-center-of-universe architecture needs to be reimagined. The problem with this architecture is that, once users are brought inside the perimeter, they are given excessive trust, and can move laterally to anywhere in the network. That’s a problem. Enterprises need to remove that excessive trust by transitioning from one macro-perimeter to several micro-perimeters or software-defined edges. These edges span across the enterprise digital footprint — from the access layer of the network to any number of endpoints: the routing layer of the network, a VM in the data center, the front door of a cloud VPC, or to the browser of a remote user. Unlike traditional architectures, these edges trust nothing by default. Similarly, they eliminate the concept of “internal” vs “external” users in the network, and instead create direct, secure connections between users and enterprise resources. Moreover, these edges communicate directly with each other to dynamically provision different types of asset and site communication models.
3. Shift to identity-based policy
The identity of an asset — user, device, application, data — is one of the most important pieces of context that can be factored into policy. Indeed, the foundational principle of Zero Trust networking is to base network access on the identity of a user, device, application, or data.
4. Manage identity-based policy centrally, enforce policy at the edge
Your Zero Trust project must be able to scale with your enterprise, which means that you need a cloud-delivered solution. Similarly, you should be able to manage identity-based policy centrally, with a cloud-based service. These policies must be created dynamically and pushed to the edge for enforcement.
5. Never trust, always verify
Zero Trust networking starts with the assumption that users are denied by default. Trust is assessed at the initiation of network connectivity — but it should not stop there. Enterprises must continuously monitor and assess the behavior of users and devices throughout the interaction, with the ability to revoke trust at any time. Ultimately, there are numerous benefits to adopting a level-headed, five-phased journey to Zero Trust — rather than trying to change everything overnight. These include:
- Greater focus. A phased approach allows your organization to focus time, budget, and efforts on solving one problem at a time — allowing you to make continuous progress towards improving the security posture of your organization. Zero Trust is a true “zero waste” strategy.
- Fuller coverage. You can ensure that Zero Trust coverage extends to all of your digital resources over time, by gradually gaining executive buy-in and support.
- Faster execution. Because you can tap the right individuals within the organization at the right time — no sooner or later — Zero Trust projects tend to begin faster and progress more quickly.
Many enterprises are struggling today with their Zero Trust journeys. To read more about how to accelerate Zero Trust in your organization, download our white paper.
No Comments Yet
Let us know what you think